Token Overview
API Token (API Key) is your credential for calling Laozhang API. Like a password, it’s used to verify your identity and record usage.Create Token
Standard Token
Log in to Console
Visit Laozhang API Console and log in
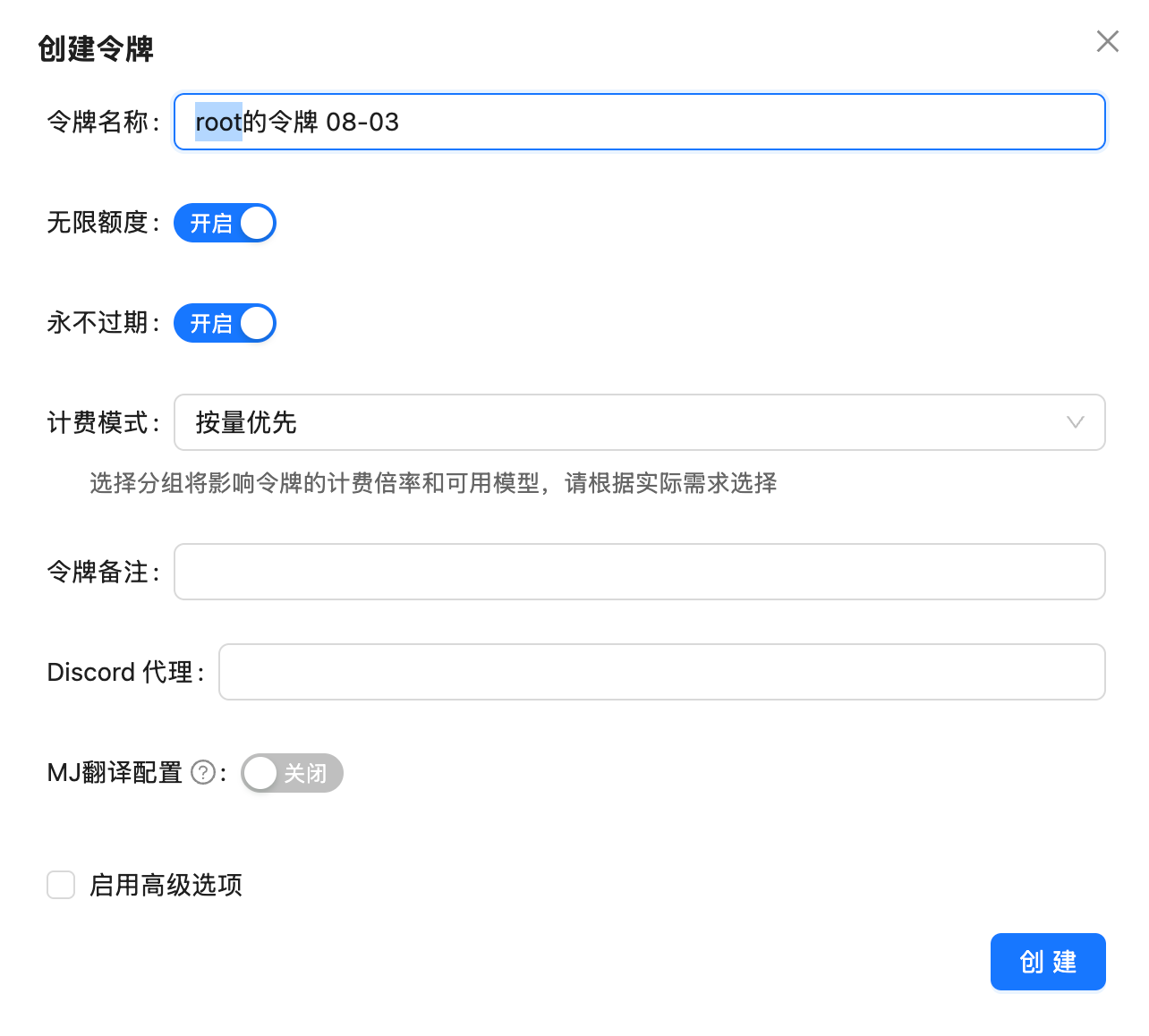
Configure Token
Fill in token information:
- Token Name: For identifying token purpose (e.g., “Production Environment”, “Testing”)
- Billing Method: Choose billing method
- Usage-based billing (pay per token)
- Pay-per-use (pay per request)
- Permissions: Set API permissions (optional)
- Expiration Time: Set token validity period (optional)
Special Purpose Tokens
- Usage-based Billing Token
- Pay-per-use Token
- Read-only Token
- Temporary Token
Suitable For:
- High-frequency API calls
- Chat applications
- Text processing
- Code generation
- Billed by tokens consumed
- More economical for high usage
- Support all text models
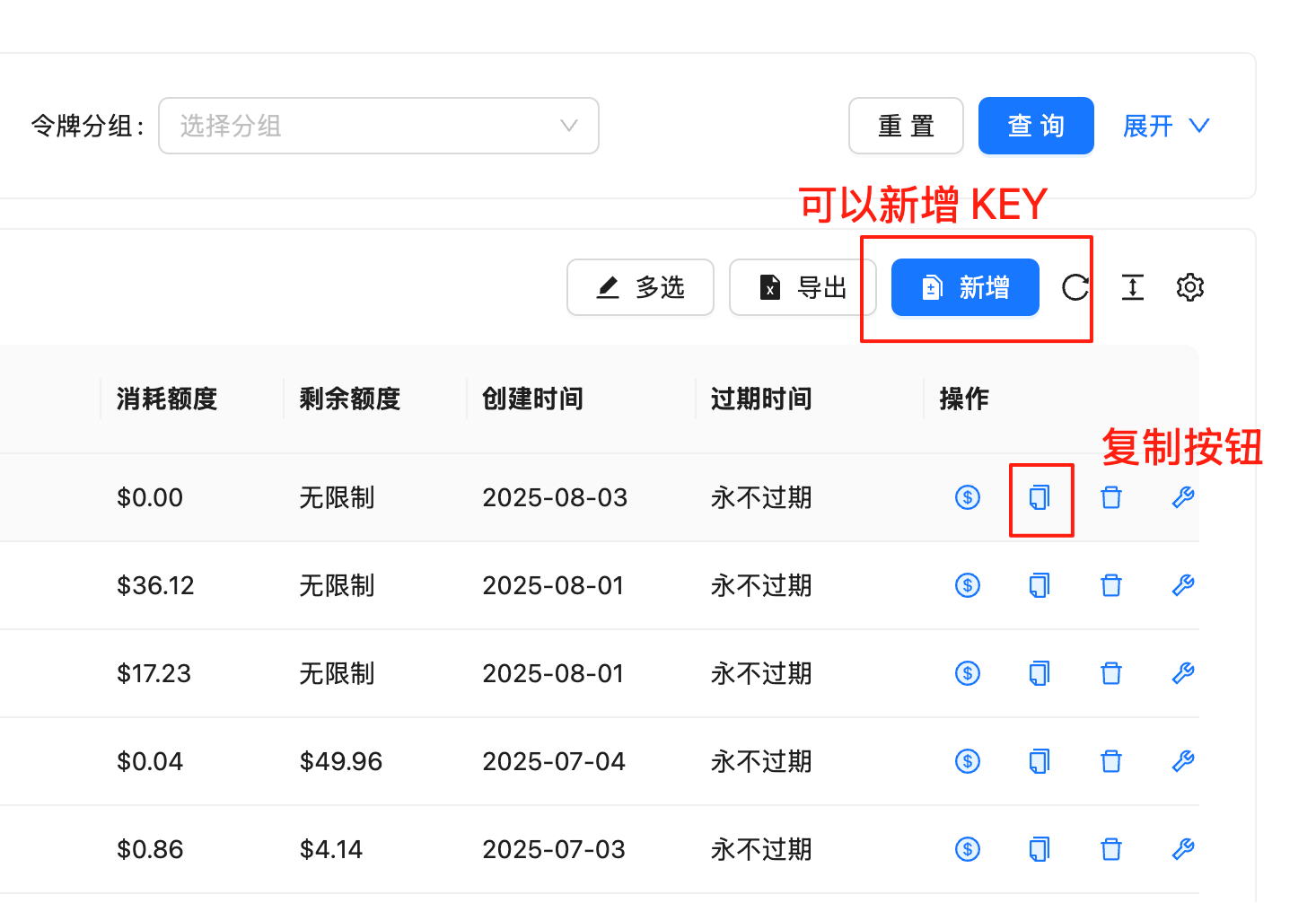
Manage Tokens
View Token List
View all your tokens in console:| Token Name | Created | Last Used | Status | Operations |
|---|---|---|---|---|
| Production | 2024-01-01 | 2 minutes ago | 🟢 Active | Edit | Revoke |
| Testing | 2024-01-05 | Yesterday | 🟢 Active | Edit | Revoke |
| Demo | 2024-01-10 | Never | 🟡 Not Used | Edit | Revoke |
| Old Token | 2023-12-01 | Last month | 🔴 Revoked | Delete |
Edit Token
Can modify token configuration:Cannot modify the token value itself. If need new Token value, must recreate.
Revoke Token
When need to invalidate a Token:Rotate Tokens
Regularly rotating Tokens enhances security:Security Best Practices
1. Token Storage
2. Version Control
3. Permission Control
Set minimum necessary permissions:| Scenario | Recommended Permissions |
|---|---|
| Production Environment | Full permissions, strict access control |
| Development Environment | Full permissions, local use only |
| Testing Environment | Limited permissions, low quotas |
| Demo Applications | Read-only or limited calls |
| Third-party Integration | Minimum necessary permissions |
4. IP Whitelist
Limit Token to specific IP addresses:Add Allowed IPs
Add IPs allowed to use this Token:
- Single IP:
192.168.1.100 - IP Range:
192.168.1.0/24 - Multiple IPs: Add multiple rules
5. Usage Monitoring
Regularly check Token usage:Token Leakage Handling
If Token Leaked
Assess Impact
Evaluate potential losses:
- Unusual API calls?
- Abnormal cost increases?
- Sensitive data leaks?
Contact Support
If unusual usage found, contact support:
- Email: support@laozhang.ai
- Request balance freeze or refund
- Report security incident
Prevent Leakage
Programmatic Management
Create Token via API
List Tokens
Revoke Token
Common Issues
Error: "Invalid API Key"
Error: "Invalid API Key"
Possible Causes:
- Token Incorrect
- Check for extra spaces or newlines when copying
- Ensure complete Token copied
- Check for character confusion (0/O, 1/l, etc.)
- Token Revoked
- Check Token status in console
- May have been manually revoked
- May have reached expiration time
- Token Expired
- Check Token expiration time
- Recreate if expired
Can one account create multiple Tokens?
Can one account create multiple Tokens?
Yes, can create multiple TokensUse Cases:
- Different environments (development/testing/production)
- Different projects
- Different billing methods
- Different permission levels
- Standard users: Up to 10 Tokens
- Professional users: Up to 50 Tokens
- Enterprise users: Unlimited
Can billing method be changed after Token creation?
Can billing method be changed after Token creation?
Cannot directly change billing methodSolutions:
- Create new Token with desired billing method
- Update applications to use new Token
- Revoke old Token
- Usage records remain independent
- Balance is shared (same account)
How to set usage limits for Token?
How to set usage limits for Token?
What to do after forgetting Token?
What to do after forgetting Token?
Cannot Retrieve Lost TokenToken only displays once when created, cannot be retrieved later for security.Solutions:
- Create new Token as replacement
- Update all applications to use new Token
- Revoke old Token (optional)
- Immediately save Token after creation
- Use password manager to store
- Save to secure configuration management system
Best Practices
1. Environment Isolation
Use different Tokens for different environments:2. Token Naming
Use clear naming conventions:3. Regular Audits
Establish regular audit mechanisms:Related Resources
- Insufficient Balance - Handle balance issues
- Usage Logs - View API usage records
- Data Security - Understand data protection
- API Reference - View API documentation